Four types of fake key attacks. Each diagram represents Alice
By A Mystery Man Writer
Last updated 15 Jul 2024
Download scientific diagram | Four types of fake key attacks. Each diagram represents Alice (left), her contacts (right), and an adversary (center). The green lines represent secure connections; the red lines represent compromised connections. Note that in each situation, there may be other pairs of clients communicating securely that are not shown. from publication: Automatic Detection of Fake Key Attacks in Secure Messaging | Popular instant messaging applications such as WhatsApp and Signal provide end-to-end encryption for billions of users. They rely on a centralized, application-specific server to distribute public keys and relay encrypted messages between the users. Therefore, they prevent | Automatism, Security and Server | ResearchGate, the professional network for scientists.

A comprehensive survey on robust image watermarking - ScienceDirect

PDF) Automatic Detection of Fake Key Attacks in Secure Messaging
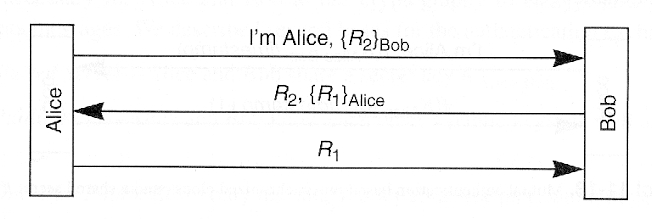
Chapter 11
What is a Man-in-the-Middle Attack: Detection and Prevention Tips
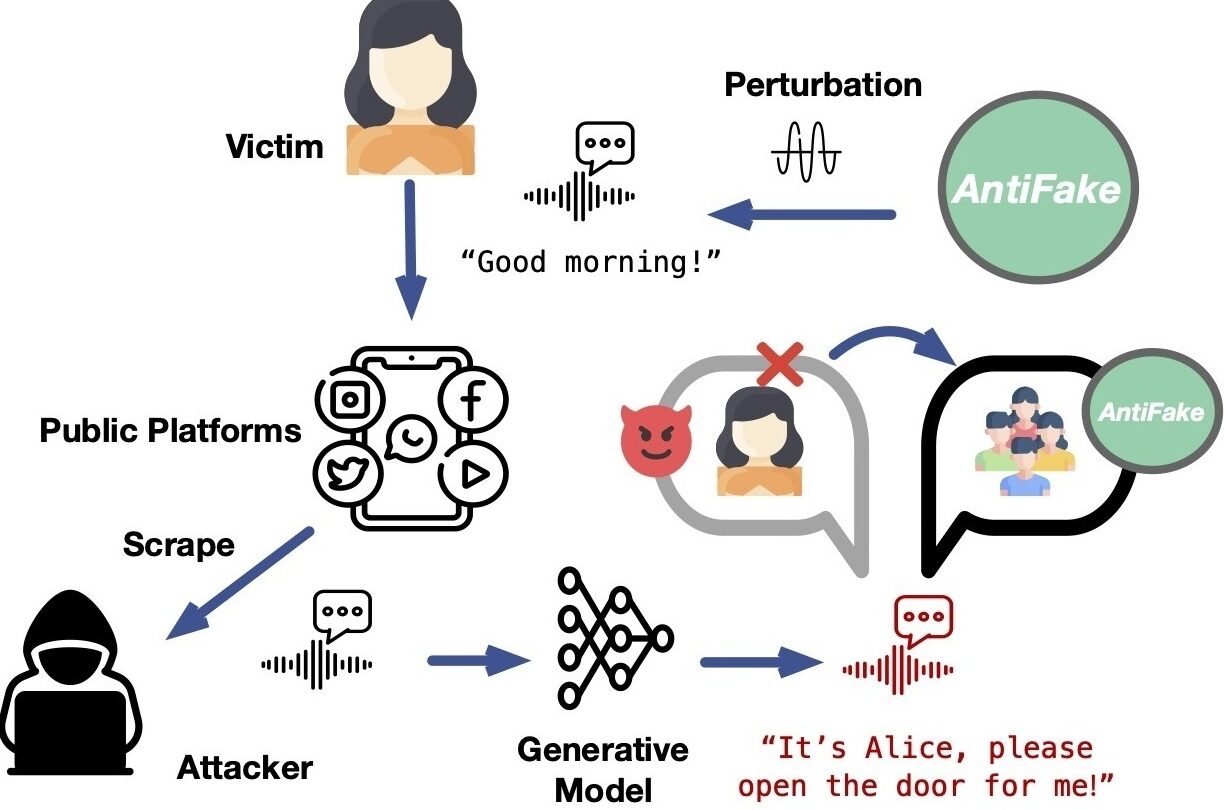
Worried about AI hijacking your voice for a deepfake? This tool could help – WABE

What Is the CIA Security Triad? Confidentiality, Integrity, Availability Explained – BMC Software
Digital signature - Wikipedia
Phishing and impersonation attacks (A 8 ) being executed, while

Kent SEAMONS Brigham Young University - Provo Main Campus, Utah

Daniel Zappala's research works Brigham Young University - Provo

Symmetric Key Cryptography - an overview

3 Different Types of Cryptography and How Each One Works - History-Computer
Recommended for you
You may also like
)

















![Canary Corrugated Cardboard Cutter Dan Chan [Fluorine Coating] Yellow Dc-190F](https://i.ebayimg.com/images/g/1FsAAOSw3FpjjelL/s-l1200.webp)