Threat Hunting - Simplifying The Beacon Analysis Process - Active
By A Mystery Man Writer
Last updated 15 Jul 2024
In part one of this two-part series, I described what is involved with performing a beacon analysis and why it is so important […]
Threat Simulator - Active Countermeasures

Enterprise Scale Threat Hunting: Network Beacon Detection with Unsupervised ML and KQL, by Mehmet Ergene, May, 2021
Beacon Analysis - The Key to Cyber Threat Hunting - Active Countermeasures

How to make threat hunting feasible, Part I: Detection - Cisco Blogs
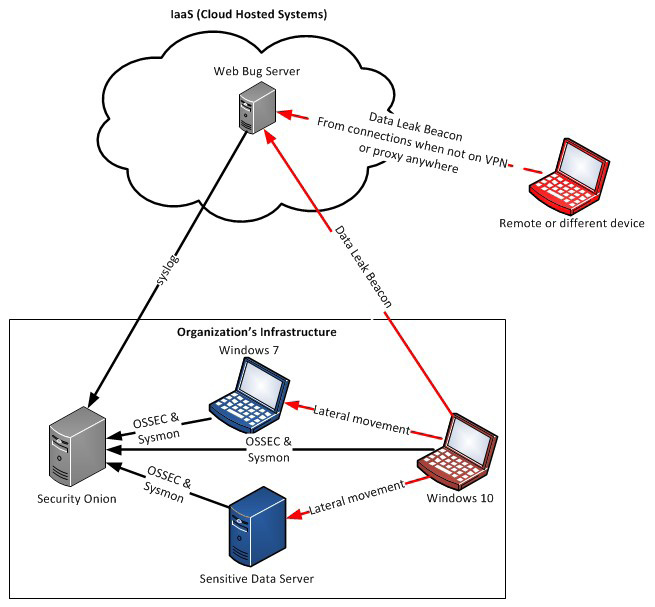
Offensive Intrusion Analysis: Uncovering Insiders with Threat Hunting and Active Defense – CSIAC
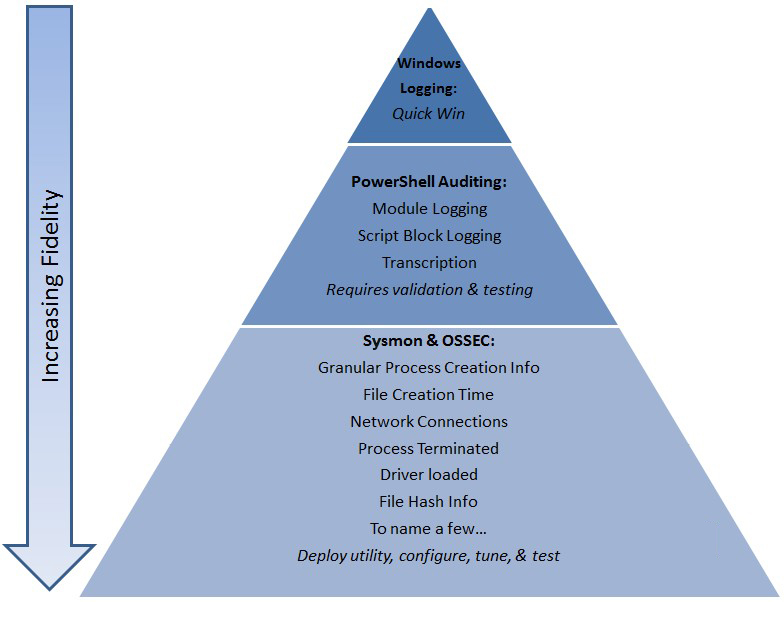
Offensive Intrusion Analysis: Uncovering Insiders with Threat Hunting and Active Defense – CSIAC

From BumbleBee to Cobalt Strike: Steps of a BumbleBee intrusion
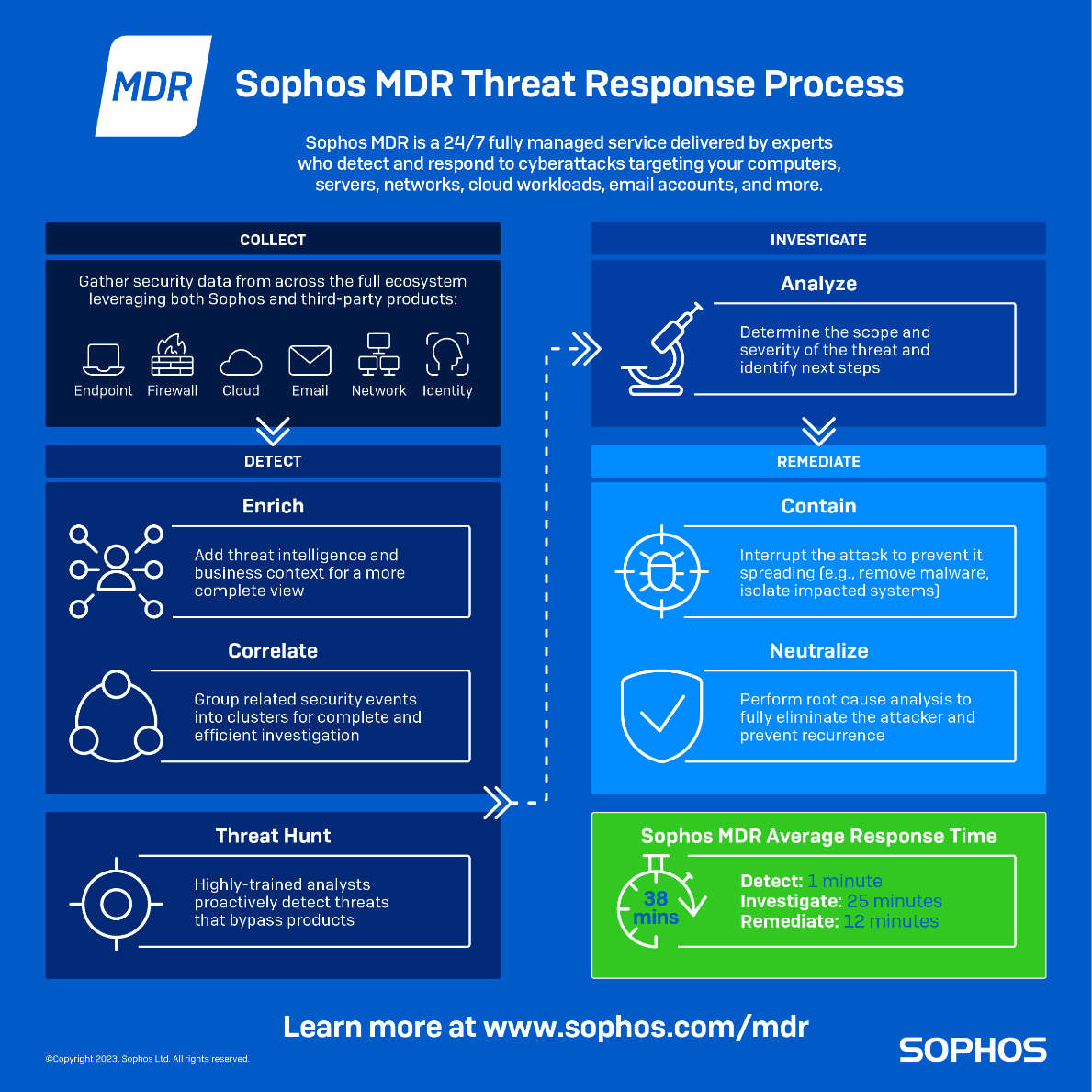
What is Threat Hunting? Threat Hunting Explained

Unveil lurking threats with Rita

Threat Hunting: Process, Methodologies, Tools And Tips

What is Cyber Threat Hunting? [Proactive Guide] - CrowdStrike
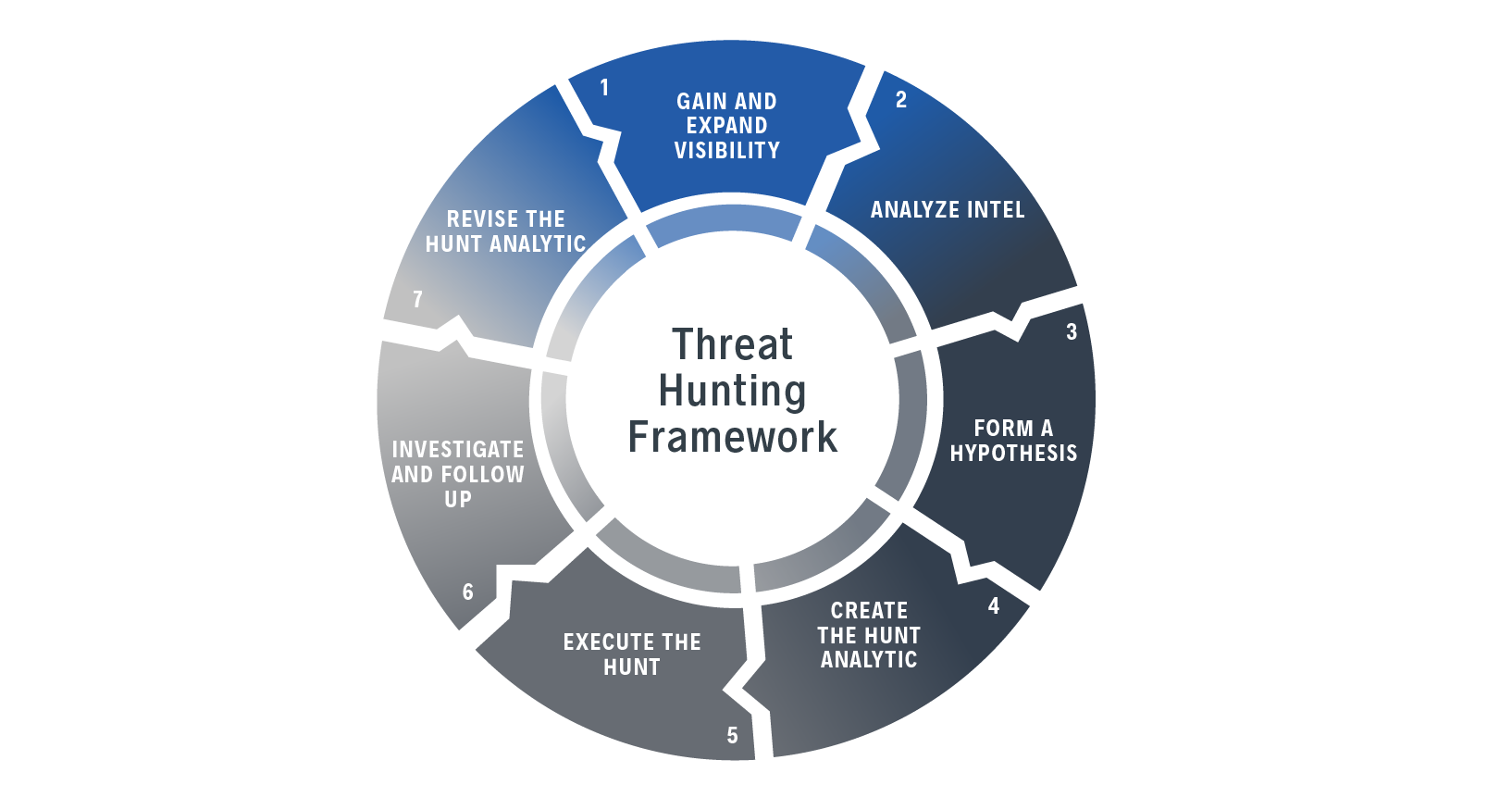
How Threat Hunting Can Evolve Your Detection Capabilities - Gigamon Blog

Threat Simulator - Active Countermeasures

Threat Hunting. Threat hunting is a proactive cyber…, by Eyüp Cebe
Recommended for you
You may also like












